Verisign released its Q3 2016 Distributed-Denial-of-Service (DDoS) Trends Report, which analyses key trends in online attacks, including attack statistics, behavioral trends and future outlook. Verisign released its Q3 2016 (July 1, 2016 through Sept. 30, 2016). This report contains the observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of, and in cooperation with, customers of Verisign DDoS Protection Services. The security research of Verisign iDefense Security Intelligence Services conducted, represents a unique view into the attack trends unfolding online, including attack statistics and behavioral trends for Q3 2016.

Key takeaways
DDoS Attacks Are Unpredictable and are becoming more challenging to all industries
The highest intensity flood attack: TCP SYN flood peaked at approximately 60 Gbps and 150 Mpps (Million Packets Per Second)
49 percent of the total attacks was UDP flood attack
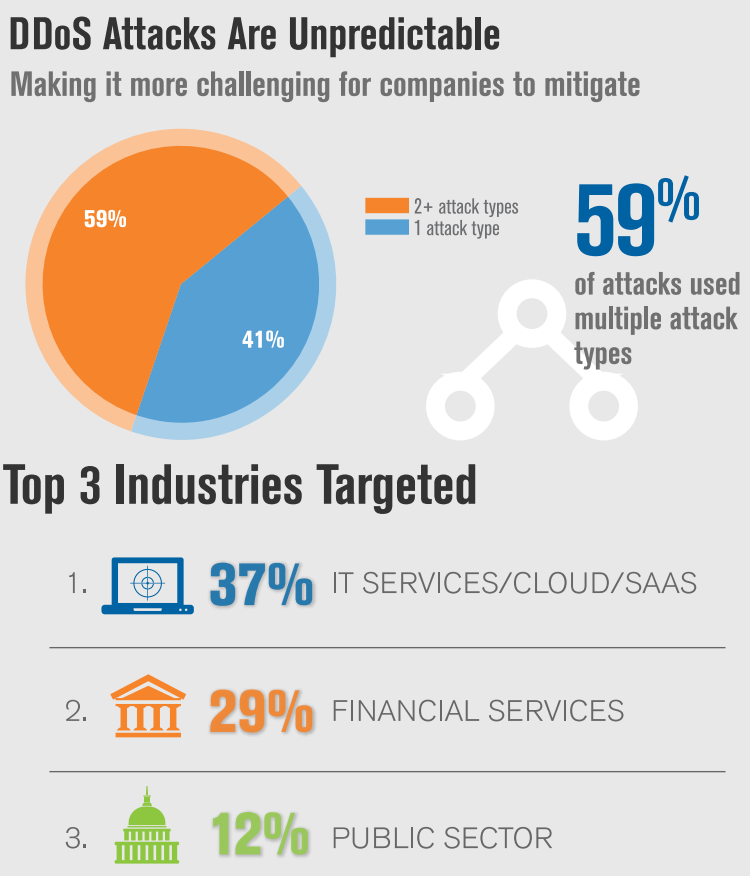
DDoS Attacks Are Unpredictable
DDoS attacks continue to be complex and unpredictable, making them more challenging for companies to mitigate. While not directly observed by Verisign, Q3 2016 was notable due to several attacks unprecedented in attack size. Specifically, the approximately 620 Gbps attack against KrebsonSecurity1 and a 579 Gbps attack reported by Arbor Networks 2 were significant and widely reported within the industry.
Attackers in Q3 2016 launched sustained and repeated attacks against their targets. In fact, out of all the Verisign customers targeted by DDoS attacks in Q3 2016, 41 percent were targeted multiple times during the quarter.
Multi-Vector DDoS Attacks Continue to Dominate
Fifty-nine percent of the DDoS attacks mitigated by Verisign in Q3 2016 employed multiple attack types indicating that DDoS attacks continue to be complex, and thus require more time and effort to mitigate.
Types of DDoS Attacks
UDP flood attacks continue to dominate in Q3 2016, making up 49 percent of the total attacks in the quarter. The most common UDP floods mitigated were Domain Name System (DNS) reflection attacks, followed by Network Time Protocol (NTP) reflection attacks.
Highest Intensity Flood and Largest Volumetric Attack
The highest intensity flood attack observed by Verisign in Q3 2016 was a TCP SYN flood that peaked at approximately 60 Gbps and 150 Mpps (Million Packets Per Second). This flood attack is one of the highest packets per second attacks ever observed by Verisign, surpassing the previous highest flood of 125 Mpps mitigated by Verisign in the fourth quarter of 2015.
The largest attack in Q3 2016 utilized the Generic Routing Encapsulation (GRE) protocol (IP protocol 47) and peaked at 250+ Gbps and 50+ Mpps. This is the first time Verisign observed this type of attack against its customer base. The attack was notable in that the attackers encapsulated UDP packets to legitimate service ports within the GRE protocol. Attackers were able to increase the payload and add volume to the attack with this technique. Both the source and destination IP addresses in the encapsulated data were spoofed. The spoofing of the IP addresses forced the network devices of the end recipient to analyze the content within the packet, which depleted the recipient’s resources while consuming processing capacity and available network bandwidth.
For more information on DDoS trends, the full report can be downloaded from here
About Verisign
Verisign, a global leader in domain names and Internet security, enables Internet navigation for many of the world’s most recognized domain names and provides protection for websites and enterprises around the world. Verisign’s Security Services include intelligence-driven Distributed Denial of Service Protection, iDefense Security Intelligence and Managed DNS.

